What is Pentesting?
In this section I will try to define some terms (without reinventing the wheel) that I came across during my studies on Pentesting using references from widely recognized brands and companies.
What is Pentesting?
Before define what is Pentesting, here some principal questions:
What is Informaction Security (infoSec)?
According to CISCO
Information security, often referred to as InfoSec, refers to the processes and tools designed and deployed to protect sensitive business information from modification, disruption, destruction, and inspection.
also according to CEH
Information security refers to the protection or safeguard of information and information systems that use, store and transmit information from unauthorized accesses, disclosures, alterations, and destructions. Information is the critical assets that organizations need to secure.
-CEH certification material
InfoSec also aplies five basic principles
- Confidentiality
- Integrity
- Availability
- Authenticity
- Non-repudiation
CIA triad:
- Confidentiality
- Integrity
- Availability
for more and detailled about Information Security see wikipedia and geeksforgeeks
What is Cybersecurity?
Cybersecurity, Computer security or Information technology security (it security). There are many definitions according to big IT brands and agencies:
Cyber security is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks.
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks.
Cybersecurity is the practice of protecting critical systems and sensitive information from digital attacks. Also known as information technology (IT) security, cybersecurity measures are designed to combat threats against networked systems and applications, whether those threats originate from inside or outside of an organization.
-IBM
Cybersecurity is the art of protecting networks, devices, and data from unauthorized access or criminal use and the practice of ensuring confidentiality, integrity, and availability of information.
Prevention of damage to, protection of, and restoration of computers, electronic communications systems, electronic communications services, wire communication, and electronic communication, including information contained therein, to ensure its availability, integrity, authentication, confidentiality, and nonrepudiation.
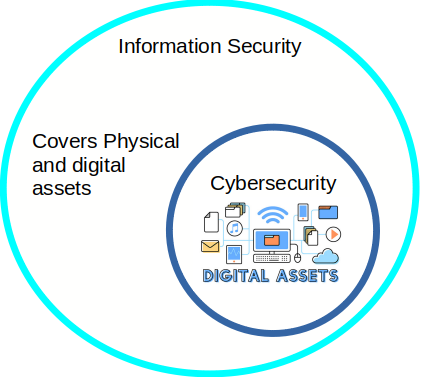
is Information Security == Cybersecurity?
- According to NIST cybersecurity ensure the five basic principles of information security
- Cybersecurity focuses only protect digital attacks
They are not very different, Cybersecurity only focuses on digital assets, while Information Security is more general
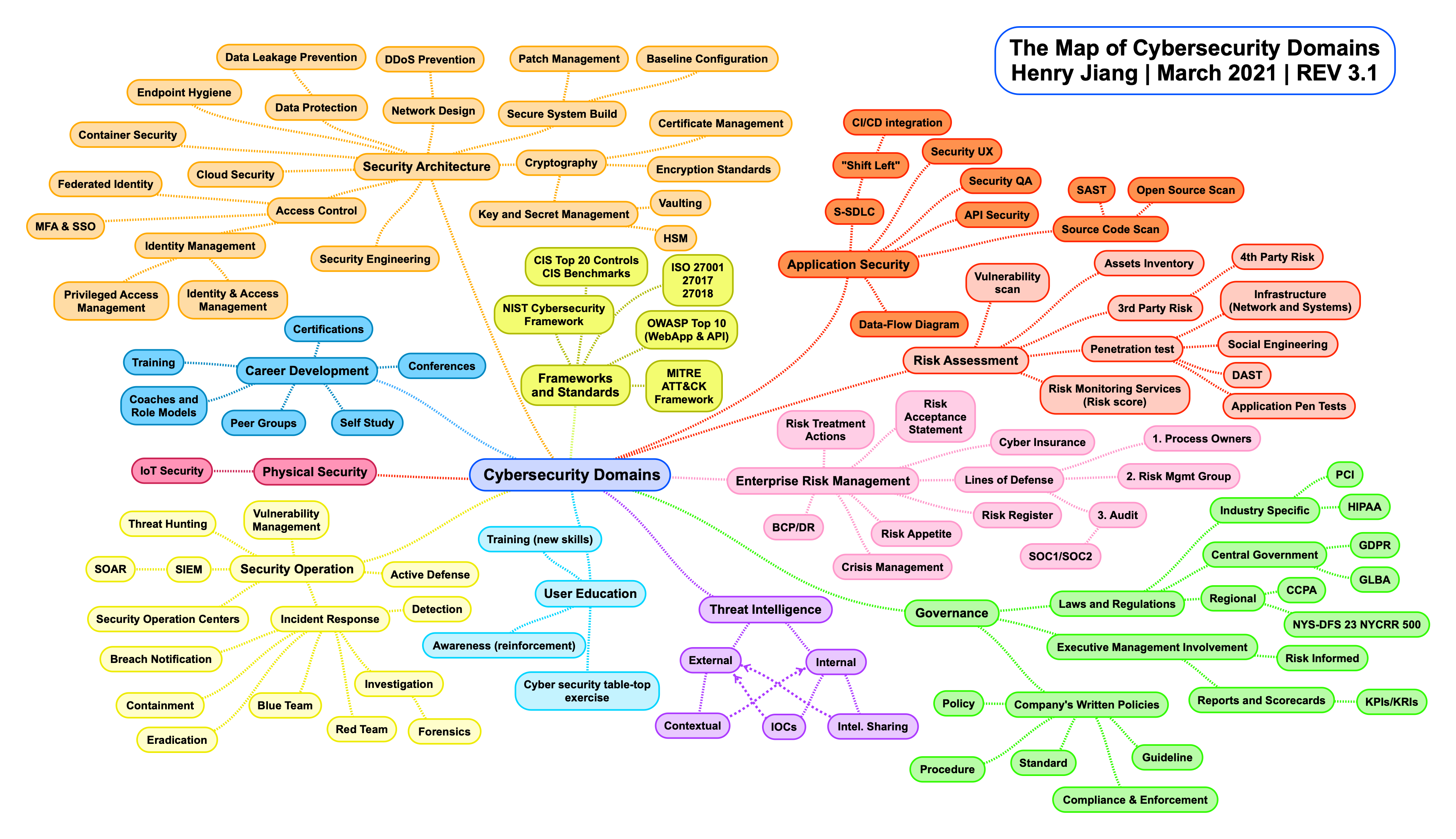
Cybersecurity domains
The main domains are:
- Network security
- Aplication security
- Cloud security
- Cryptography
- Infrastructure security
- Incident response
- Vulnerability management
Also Cybersecurity covers many domains as we can see in the following image:
now, What is Pentesting?
We can found on CEH certification material an correct definition about what is Pentesting
Penetration testing is a method of evaluating the security of an information system or network by simulating an attack to find out vulnerabilities that attacker could exploit. Penetration test (or “pen-testing”) exposes the gaps in the security model of an arganization and helps organizations reach a balance between technical prowess and business functionality form the perspective of potential security breaches.
-CEH certification material
now we know about what is Pentesting let’s define what is Pentester
What is a pentester?
From the awesome book The pentester blueprint
Pentesters assess the security of computers, networks, and websites by looking for and exploiting vulnerabilities, commonly knows as hacking
In the next post we define what is hacking and hacker and what can they do.




