Web Simplay walkthrough
The past weekend, Synack Red Team was starting his invitational CTF
We are excited to support the @SynackRedTeam Five #CTF!
— Hack The Box (@hackthebox_eu) November 1, 2021
You still have time to register and hack some great #HTB challenges: https://t.co/ORiXH0p6mH
$2,800 in prizes! Including an exclusive Challenge Coin by #HTB & #SRT 🎁#HackTheBox #CaptureTheFlag #CyberSecurity #Hacking pic.twitter.com/nY9Cu2qtp7
The CTF contained several challenges:
- Crypto
- Forensic
- Misc
- Pwn
- Reversing
- Web
My problem was the days 5-7. I was in my work and I don’t had time to solve these challenges
but all the challenges were downloadable. In this post I’ll solve the challenge “Simplay” here the walkthrough.
Al challenges are here
The challenge
The challenge title said:
The agency has picked up on an addictive mobile application that predicts when someone will find love. We suspect foul play by the evil company behind this obvious scheme. We think that they will try to have this application installed on every device in the world, in order to mind control it’s users. Agent, we need you to infiltrate the recent website they launched and save the world.
Web_Simplay, what does it do ?
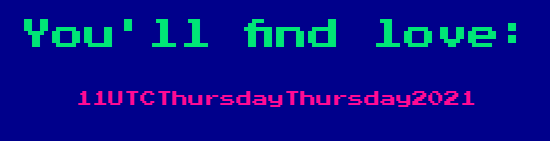
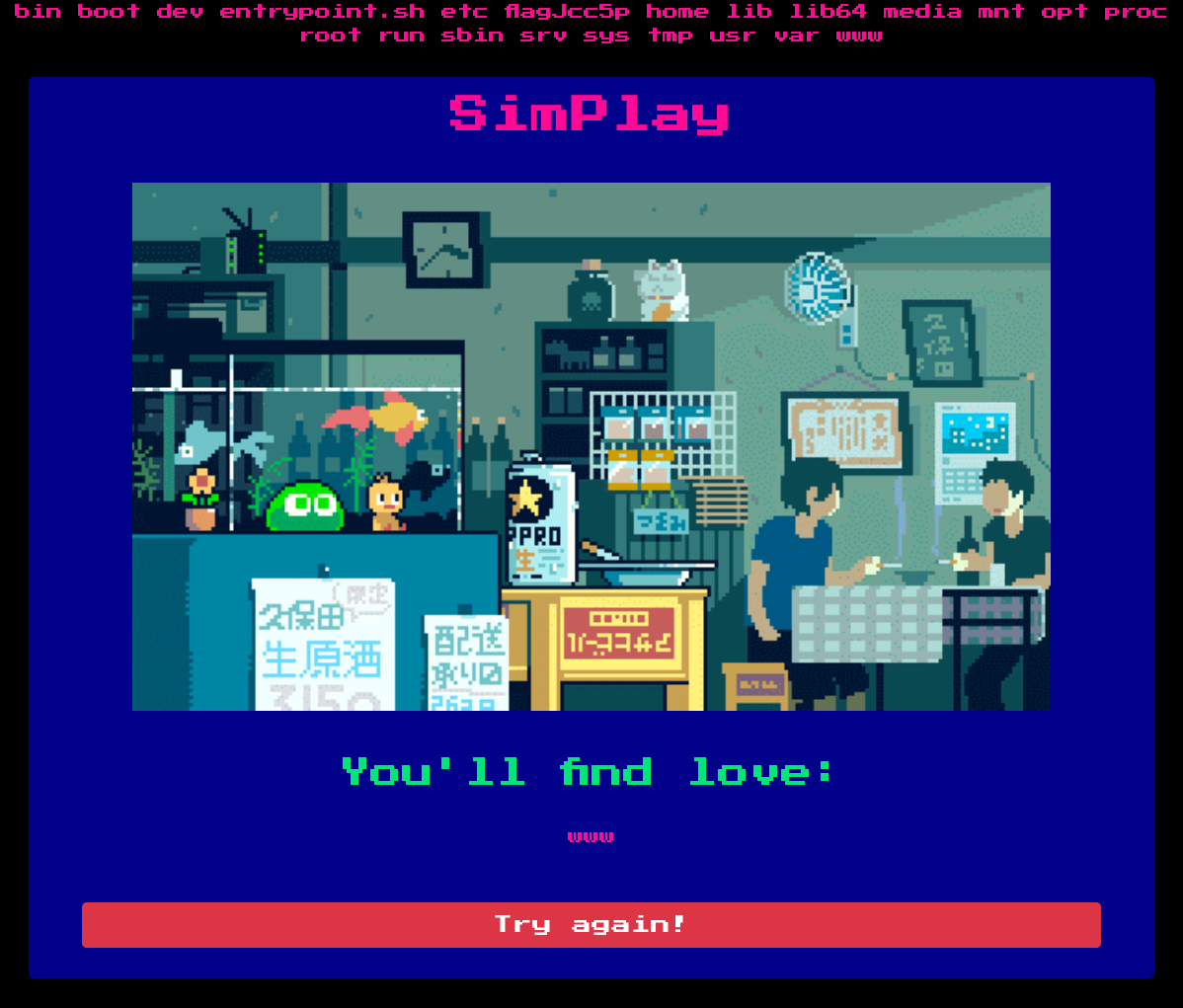
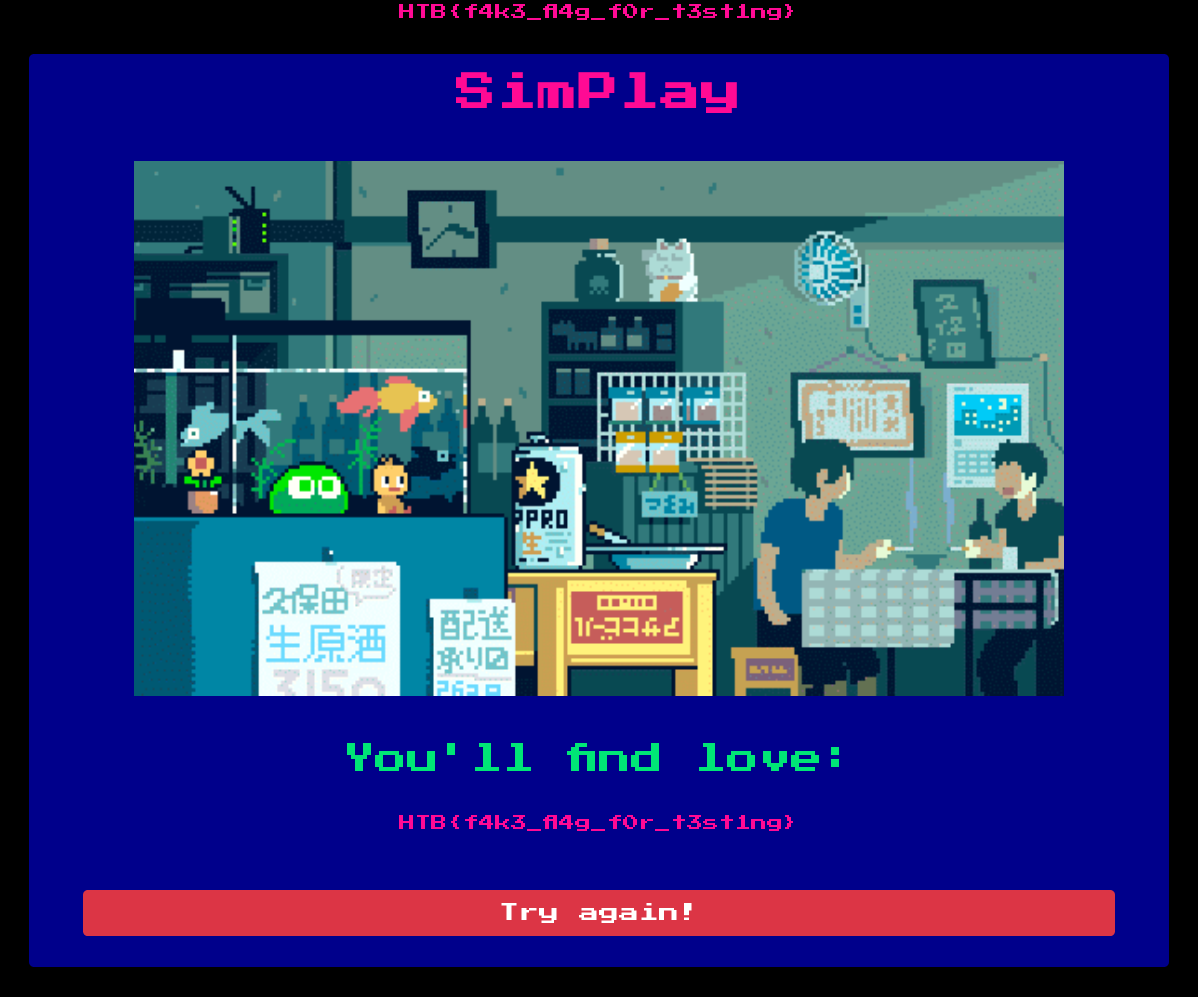
Web_Simplay is simple website, It displays this:

It only contains a button “Try again”, when it is clicked it sends a get request with “r” value by default
|
|
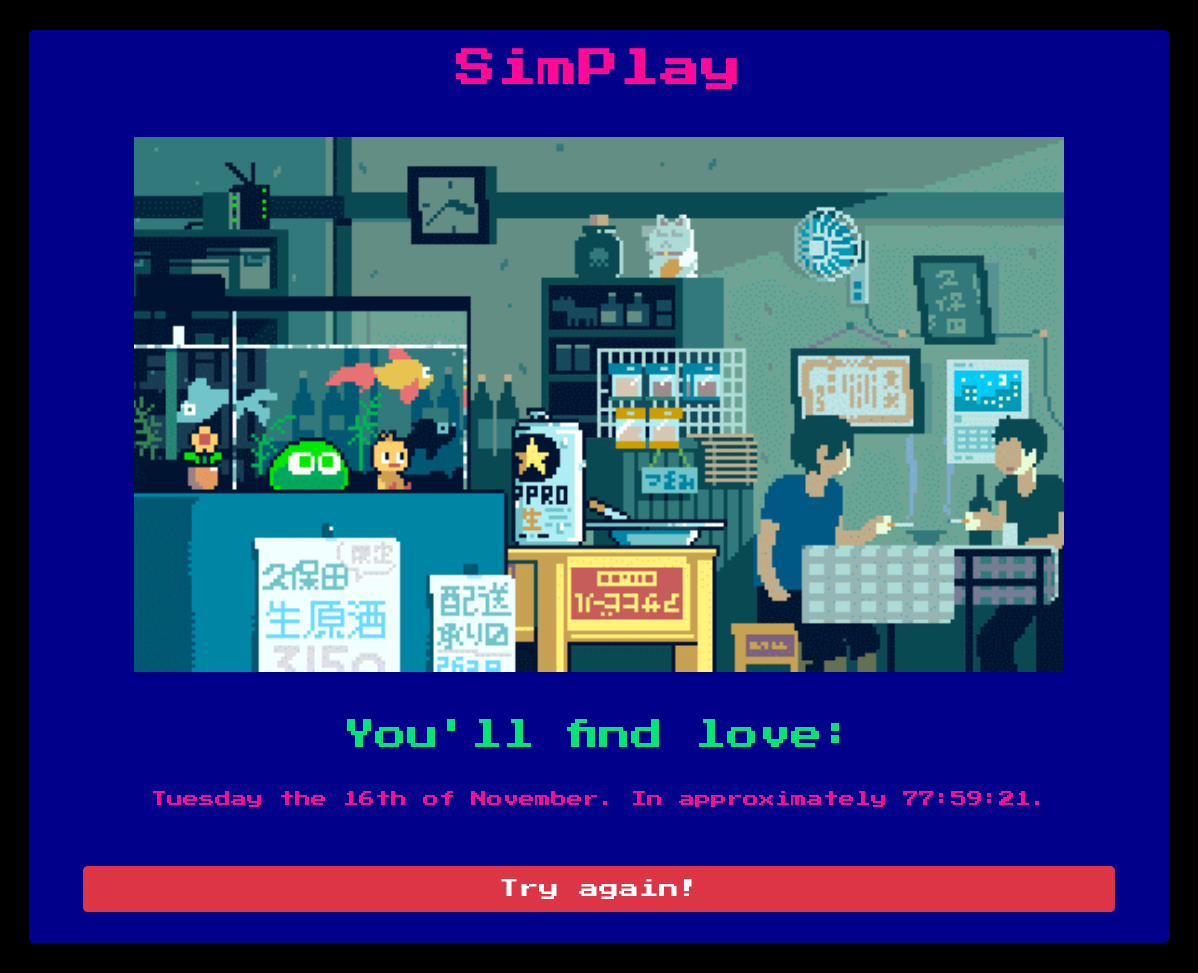
When we try to change the ‘r’ value, the website change the love message. For example, when we try this:
|
|
We get this:
Getting the Flag
This challenge give us source code, the interesting file are:
- “TimeController.php” in charge of take get request from user and store it in “$format” variable
- “TimeModel.php” in charge of generate date and show to client using “$format” variable
If check in detail the file “TImeModel.php” in the line 14 it uses “eval” function, that is the key for this challenge because it executes PHP code as string and store it in “$time” variable, that variable show us the time when we’ll find the love.
Bypass eval() function to get RCE
To bypass the eval function() only replace the contents of “$time” variable and comment de next one character’s yes similar to SQL injection but not equal let see the code:
|
|
The above request show us:
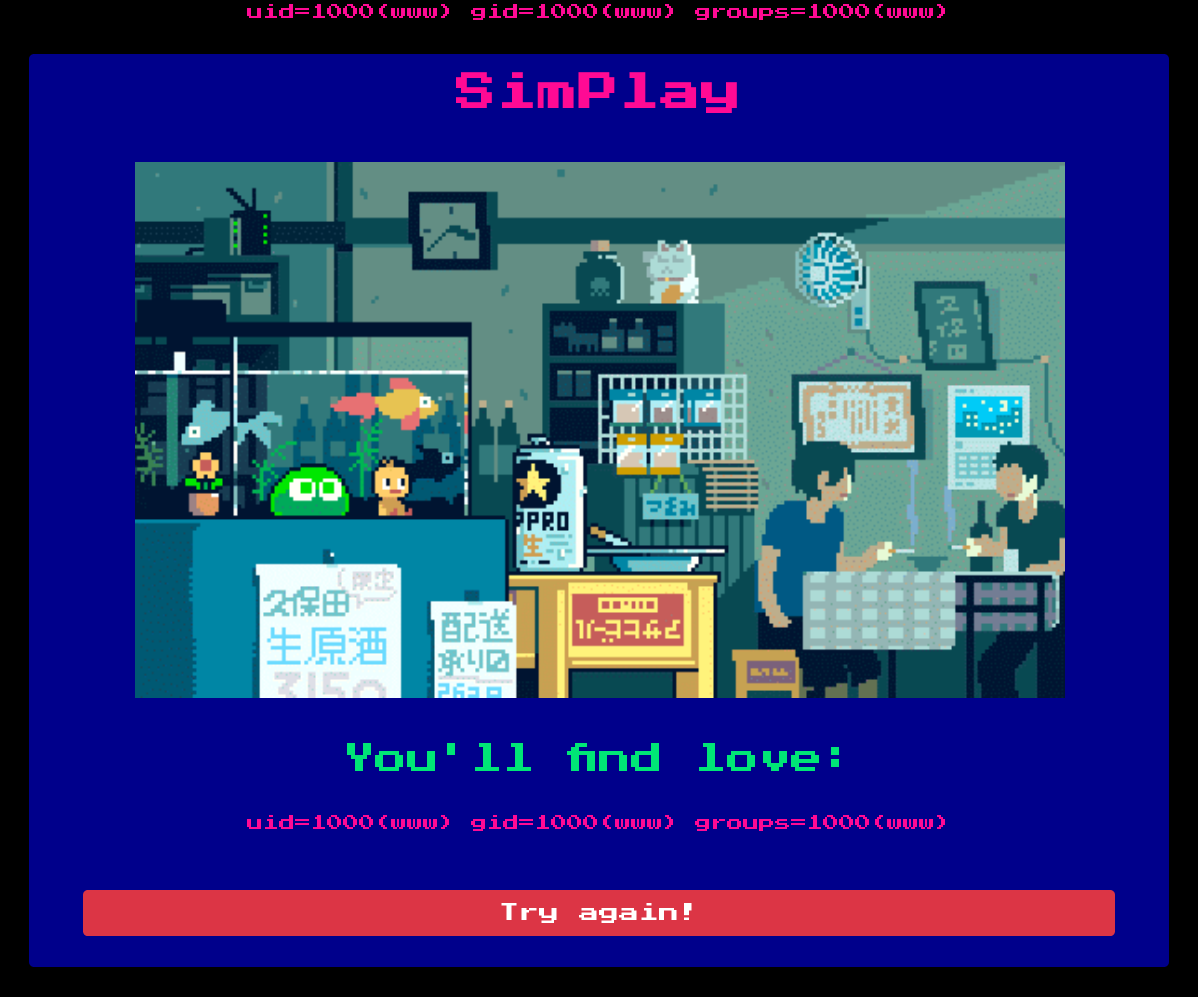
Now we are ensured the eval function is bypassed, the script “entrypoint.sh” move the flag from /var/www to / the next request list the / dir
|
|
Finally, we getting the flag with:
|
|
Notes
Another form to get RCE in this challenge is using:
|
|
- ls with backticks it’s a execution operator
- “print” prints only one argument and always return 1
- ${} use to evaluate an expression
- if you try in PHP shell:
|
|
you get the “ls” output and finally the error:
|
|
because print always return 1
Happy hacking!!!!