Lab0: Adding external device and local host
Now that the lab is almost complete, we still need to add a wireless access point to the public network. To do this, we will use an OpenWrt router or any router you have on hand. The procedure for adding a physical device to GNS3 (in this case, a wireless router with OpenWrt) is described in the following video:
As mentioned, any external device can be added to GNS3, you just need an additional Ethernet port. On the device side, the network is configured like any other network, either WAN or LAN. A more detailed description can be found in the book:
Lab0: Vlans and ACL's
Following the previous post, we will now add Vlans and ACL’s to add an extra layer of security.
ACL’s
The Public, Administrative, and Development networks can communicate with each other. To avoid this, we will add ACL’s to R1. We create rules for each network:
Public Network
For this network, we need to deny routing to the Administrative and Development networks. We create an access-list 2:
|
|
Now, on the interface for this network on R1:
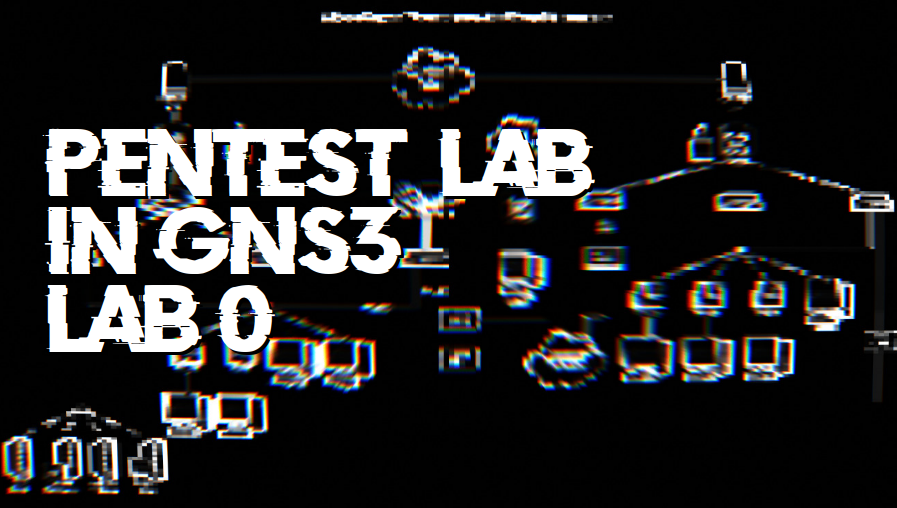
Lab0: Setup Pentesting Lab in GNS3
Overview
This document will guide you through the process of designing and implementing a pentesting laboratory using GNS3 as the primary tool.
Network Architecture
For the network design, we will consider a small organization that requires:
- A network for servers exposed to the internet
- A public network where clients can connect to the internet via cable or Wi-Fi
- A network for administrative personnel
- A network for developers
As seen, we have 4 groups or subnets. Some additional conditions are:
Pentesting Lab in GNS3
Introduction
After completing my CCNA1 course, I decided to set up my own Pentesting lab or controlled environment, but with the condition that it should be as realistic as possible. I still have a lot to l earn about the CCNA 200-301 certification, and what better way to practice what I’ve learned than by working on this project. Additionally, this will be my first official project in the field of cybersecurity.
Solving Jangow01 using only Bash
I solved Jangow01 using only Bash!!!
In this series of posts, I try to use only Bash and some external tools only if extremely needed.
Web Simplay walkthrough
The past weekend, Synack Red Team was starting his invitational CTF